It leads me to believe they have paid the ransom and are trying to downplay the severity of this whole mess.
Or they are fucking insane and are "fighting" with the attacker while not telling their customers anything.
Either way, I would never do business with them. They are absolutely incompetent and do not care about their customers security.
I’m a bit late to the thread and my brain is scattered a little on the subject. But I wanted to add what seems to me to also be plausible:
That the hacker in question never compromised them at all and simply made a false claim. He doesn’t seem very reliable.
Brother, they literally admitted to getting breached a few posts above it. Its also been confirmed in "providers forum" on OGF, they are in the spreadsheet with other compromised providers.
"SQL Dumped" stands for "leaked", their database is in possession of attackers.
Take note you have not seen us on here or other similar forums lately, because we have had our hands full dealing with these two issues. Security and client services being operational has been our only concerns since that time period. Heck, we had minimal Black Friday and year end sales presence, because we were dealing with the VPS platform issues since late November...and that hurts. That was one of the most talented hacker(s) I have seen in my 30+ years in the industry. Hate them, but still impressed by their skills. The WHMCS breach I don't think was as much skill as it was luck or happening across 3rd party software flaw(s). We are finally just this weekend able to come up for air, and start working on next steps beyond security and re-install work.
~ SMARTHOST
So lets assume "ddos/hack" issue was separate from WHMCS breach "issue".
Its even more embarrassing this way, you got pwned 2 times in the same month. Presumably by 2 different attackers, both getting access to personal information and data of your customers.
First by someone who got access to VM's and client data on it, and then by someone who got access to people personal info from WHMCS.
Absolute fucking shitshow. Worst part is you didn't notify your clients about WHMCS breach, which was at this point close to a month ago. You could've send a notification, you could've submitted the data to HIBP, but you did none of that.
My recommendation from the other thread stays the same, stay away from this provider, they do not take personal information and security seriously. I have no idea what legal regulations are in the State you are located in, but some require to disclose a breach up to 2 weeks.
In EU you would've gotten sued to shit for all of that.
It leads me to believe they have paid the ransom and are trying to downplay the severity of this whole mess.
Or they are fucking insane and are "fighting" with the attacker while not telling their customers anything.
Either way, I would never do business with them. They are absolutely incompetent and do not care about their customers security.
I’m a bit late to the thread and my brain is scattered a little on the subject. But I wanted to add what seems to me to also be plausible:
That the hacker in question never compromised them at all and simply made a false claim. He doesn’t seem very reliable.
Well there's that pesky customer database dump that was being passed around, right? Or are you thinking that came from a different source?
I guess I missed that. Tough to keep up. But I still don’t see it in that telegram channel, looking at files going back to Dec 26.
Do everything as though everyone you’ll ever know is watching.
It leads me to believe they have paid the ransom and are trying to downplay the severity of this whole mess.
Or they are fucking insane and are "fighting" with the attacker while not telling their customers anything.
Either way, I would never do business with them. They are absolutely incompetent and do not care about their customers security.
I’m a bit late to the thread and my brain is scattered a little on the subject. But I wanted to add what seems to me to also be plausible:
That the hacker in question never compromised them at all and simply made a false claim. He doesn’t seem very reliable.
Well there's that pesky customer database dump that was being passed around, right? Or are you thinking that came from a different source?
I guess I missed that. Tough to keep up. But I still don’t see it in that telegram channel, looking at files going back to Dec 26.
All that was done so far was their WHMCS config and license getting leaked.
Attacker said he wont leak the entire database because "SmartHost notified the customers", I don't think he will be pleased to hear they didn't.
It leads me to believe they have paid the ransom and are trying to downplay the severity of this whole mess.
Or they are fucking insane and are "fighting" with the attacker while not telling their customers anything.
Either way, I would never do business with them. They are absolutely incompetent and do not care about their customers security.
I’m a bit late to the thread and my brain is scattered a little on the subject. But I wanted to add what seems to me to also be plausible:
That the hacker in question never compromised them at all and simply made a false claim. He doesn’t seem very reliable.
Brother, they literally admitted to getting breached a few posts above it. Its also been confirmed in "providers forum" on OGF, they are in the spreadsheet with other compromised providers.
"SQL Dumped" stands for "leaked", their database is in possession of attackers.
Take note you have not seen us on here or other similar forums lately, because we have had our hands full dealing with these two issues. Security and client services being operational has been our only concerns since that time period. Heck, we had minimal Black Friday and year end sales presence, because we were dealing with the VPS platform issues since late November...and that hurts. That was one of the most talented hacker(s) I have seen in my 30+ years in the industry. Hate them, but still impressed by their skills. The WHMCS breach I don't think was as much skill as it was luck or happening across 3rd party software flaw(s). We are finally just this weekend able to come up for air, and start working on next steps beyond security and re-install work.
~ SMARTHOST
So lets assume "ddos/hack" issue was separate from WHMCS breach "issue".
Its even more embarrassing this way, you got pwned 2 times in the same month. Presumably by 2 different attackers, both getting access to personal information and data of your customers.
First by someone who got access to VM's and client data on it, and then by someone who got access to people personal info from WHMCS.
Absolute fucking shitshow. Worst part is you didn't notify your clients about WHMCS breach, which was at this point close to a month ago. You could've send a notification, you could've submitted the data to HIBP, but you did none of that.
My recommendation from the other thread stays the same, stay away from this provider, they do not take personal information and security seriously. I have no idea what legal regulations are in the State you are located in, but some require to disclose a breach up to 2 weeks.
In EU you would've gotten sued to shit for all of that.
It leads me to believe they have paid the ransom and are trying to downplay the severity of this whole mess.
Or they are fucking insane and are "fighting" with the attacker while not telling their customers anything.
Either way, I would never do business with them. They are absolutely incompetent and do not care about their customers security.
I’m a bit late to the thread and my brain is scattered a little on the subject. But I wanted to add what seems to me to also be plausible:
That the hacker in question never compromised them at all and simply made a false claim. He doesn’t seem very reliable.
Brother, they literally admitted to getting breached a few posts above it. Its also been confirmed in "providers forum" on OGF, they are in the spreadsheet with other compromised providers.
"SQL Dumped" stands for "leaked", their database is in possession of attackers.
Take note you have not seen us on here or other similar forums lately, because we have had our hands full dealing with these two issues. Security and client services being operational has been our only concerns since that time period. Heck, we had minimal Black Friday and year end sales presence, because we were dealing with the VPS platform issues since late November...and that hurts. That was one of the most talented hacker(s) I have seen in my 30+ years in the industry. Hate them, but still impressed by their skills. The WHMCS breach I don't think was as much skill as it was luck or happening across 3rd party software flaw(s). We are finally just this weekend able to come up for air, and start working on next steps beyond security and re-install work.
~ SMARTHOST
So lets assume "ddos/hack" issue was separate from WHMCS breach "issue".
Its even more embarrassing this way, you got pwned 2 times in the same month. Presumably by 2 different attackers, both getting access to personal information and data of your customers.
First by someone who got access to VM's and client data on it, and then by someone who got access to people personal info from WHMCS.
Absolute fucking shitshow. Worst part is you didn't notify your clients about WHMCS breach, which was at this point close to a month ago. You could've send a notification, you could've submitted the data to HIBP, but you did none of that.
My recommendation from the other thread stays the same, stay away from this provider, they do not take personal information and security seriously. I have no idea what legal regulations are in the State you are located in, but some require to disclose a breach up to 2 weeks.
In EU you would've gotten sued to shit for all of that.
How did you get access to the spreadsheet?
So Biloh didn't tell anyone about the breach?
/s
It was circulating in certain communities for quite some time now, this screenshot is all I have. I had details on exploits used and how to deploy them a long time ago as well
Information should be free. Its on providers for not taking security seriously and not patching in time.
You shouldn't think "providers section" is private in any shape or form, given enough resources anyone can get access to whatever they want. Getting "Host Rep" on non-existent hosting provider isn't hard either.
It leads me to believe they have paid the ransom and are trying to downplay the severity of this whole mess.
Or they are fucking insane and are "fighting" with the attacker while not telling their customers anything.
Either way, I would never do business with them. They are absolutely incompetent and do not care about their customers security.
I’m a bit late to the thread and my brain is scattered a little on the subject. But I wanted to add what seems to me to also be plausible:
That the hacker in question never compromised them at all and simply made a false claim. He doesn’t seem very reliable.
Brother, they literally admitted to getting breached a few posts above it. Its also been confirmed in "providers forum" on OGF, they are in the spreadsheet with other compromised providers.
"SQL Dumped" stands for "leaked", their database is in possession of attackers.
Take note you have not seen us on here or other similar forums lately, because we have had our hands full dealing with these two issues. Security and client services being operational has been our only concerns since that time period. Heck, we had minimal Black Friday and year end sales presence, because we were dealing with the VPS platform issues since late November...and that hurts. That was one of the most talented hacker(s) I have seen in my 30+ years in the industry. Hate them, but still impressed by their skills. The WHMCS breach I don't think was as much skill as it was luck or happening across 3rd party software flaw(s). We are finally just this weekend able to come up for air, and start working on next steps beyond security and re-install work.
~ SMARTHOST
So lets assume "ddos/hack" issue was separate from WHMCS breach "issue".
Its even more embarrassing this way, you got pwned 2 times in the same month. Presumably by 2 different attackers, both getting access to personal information and data of your customers.
First by someone who got access to VM's and client data on it, and then by someone who got access to people personal info from WHMCS.
Absolute fucking shitshow. Worst part is you didn't notify your clients about WHMCS breach, which was at this point close to a month ago. You could've send a notification, you could've submitted the data to HIBP, but you did none of that.
My recommendation from the other thread stays the same, stay away from this provider, they do not take personal information and security seriously. I have no idea what legal regulations are in the State you are located in, but some require to disclose a breach up to 2 weeks.
In EU you would've gotten sued to shit for all of that.
How did you get access to the spreadsheet?
So Biloh didn't tell anyone about the breach?
/s
It was circulating in certain communities for quite some time now, this screenshot is all I have. I had details on exploits used and how to deploy them a long time ago as well
Information should be free. Its on providers for not taking security seriously and not patching in time.
You shouldn't think "providers section" is private in any shape or form, given enough resources anyone can get access to whatever they want. Getting "Host Rep" on non-existent hosting provider isn't hard either.
It leads me to believe they have paid the ransom and are trying to downplay the severity of this whole mess.
Or they are fucking insane and are "fighting" with the attacker while not telling their customers anything.
Either way, I would never do business with them. They are absolutely incompetent and do not care about their customers security.
I’m a bit late to the thread and my brain is scattered a little on the subject. But I wanted to add what seems to me to also be plausible:
That the hacker in question never compromised them at all and simply made a false claim. He doesn’t seem very reliable.
Brother, they literally admitted to getting breached a few posts above it. Its also been confirmed in "providers forum" on OGF, they are in the spreadsheet with other compromised providers.
"SQL Dumped" stands for "leaked", their database is in possession of attackers.
Take note you have not seen us on here or other similar forums lately, because we have had our hands full dealing with these two issues. Security and client services being operational has been our only concerns since that time period. Heck, we had minimal Black Friday and year end sales presence, because we were dealing with the VPS platform issues since late November...and that hurts. That was one of the most talented hacker(s) I have seen in my 30+ years in the industry. Hate them, but still impressed by their skills. The WHMCS breach I don't think was as much skill as it was luck or happening across 3rd party software flaw(s). We are finally just this weekend able to come up for air, and start working on next steps beyond security and re-install work.
~ SMARTHOST
So lets assume "ddos/hack" issue was separate from WHMCS breach "issue".
Its even more embarrassing this way, you got pwned 2 times in the same month. Presumably by 2 different attackers, both getting access to personal information and data of your customers.
First by someone who got access to VM's and client data on it, and then by someone who got access to people personal info from WHMCS.
Absolute fucking shitshow. Worst part is you didn't notify your clients about WHMCS breach, which was at this point close to a month ago. You could've send a notification, you could've submitted the data to HIBP, but you did none of that.
My recommendation from the other thread stays the same, stay away from this provider, they do not take personal information and security seriously. I have no idea what legal regulations are in the State you are located in, but some require to disclose a breach up to 2 weeks.
In EU you would've gotten sued to shit for all of that.
How did you get access to the spreadsheet?
So Biloh didn't tell anyone about the breach?
/s
It was circulating in certain communities for quite some time now, this screenshot is all I have. I had details on exploits used and how to deploy them a long time ago as well
Information should be free. Its on providers for not taking security seriously and not patching in time.
You shouldn't think "providers section" is private in any shape or form, given enough resources anyone can get access to whatever they want. Getting "Host Rep" on non-existent hosting provider isn't hard either.
That spreadsheet is just gathering and findings. We dont know if the attacker gained full access to db/configuration file.
EDIT: Attacker dumped configuration files of Letbox and Smarthost on TG.
is this proof that letbox got hacked?
Probably. But if you wanted to play devil's advocate, faking a configuration.php file would be like no effort. So, to be fair, probably based on what we've seen thus far but it's not impossible that they didn't.
Do everything as though everyone you’ll ever know is watching.
Notice of Cybersecurity Incident
Attn: John Doe -
We are writing to notify you of a recent event that may have impacted your personal information.
At this time, we have no indication of fraudulent use of your personal information as a result of this incident.
Nevertheless, we are notifying you out of an abundance of caution to explain the circumstances as we understand them.
What Happened
SmartHost LLC recently became aware in late December 2023 of a cybersecurity incident impacting its client/billing platform.
An individual(s) accessed SmartHost's client/billing system administrative areas without authorization, including gaining access via a 3rd party vendor module.
The individual(s) claimed to have downloaded customer data from SmartHost's computer systems, then threatened to post and disclose the data on an Internet forum.
Upon being made initially aware of a potential breach, SmartHost immediately began an investigation into the incident.
Although no data has been released that we have seen by this individual(s) as of this time, SmartHost has determined the client/billing system was indeed breached.
What information was potentially accessed?
The compromised data would include client names, address information, phone numbers, email addresses, user names, and account/service passwords
SmartHost does not store financial information on this platform, such as credit/debit card information, which would be stored directly with our 3rd party credit card processor.
SmartHost does not have any more sensitive information about our client base such as financial information, social security numbers, ID numbers, drivers license information, etc...
What We Are Doing
We take the security of our customers’ data seriously, and after SmartHost became aware of the event, we took immediate measures to investigate and remediate the incident.
We have implemented additional safeguards to improve security related to 3rd party software/modules, and the client/billing platform as a whole.
When SmartHost was made aware of the potential breach, we immediately performed global password resets for all client accounts and the server/service passwords that we could.
We also updated all internal system access methods/connectivity.
We have also hired external security consultants to review the matter and assist as well.
Please be assured that we take data security and confidentiality very seriously.
Steps SmartHost has taken to implement additional layers of security (not necessarily in this order):
Identified/removed the primary vulnerability associated with this incident
Global password resets for all users/systems
Update platform security settings and access credentials
Collaborated with cybersecurity specialists to review the situation
Reinstall clean system platform
Notified client base about the incident
Strengthen login credentials/methods and continue to enhance login protocols/procedures and other security measures
Continuing to monitor the situation and investigate this incident
Why did it take SmartHost so long to notify me about this?
SmartHost’s investigation is ongoing. As soon as SmartHost learned that its environment had been accessed by an unauthorized party, SmartHost immediately commenced the investigation, including working with third-party security consultants. System lockdowns were immediately implemented even before we could completely verify the breach. Simultaneously, SmartHost was dealing with another security issue at the same time, including DDOS/hack attempts against our VPS service platform, and we were unsure how/if the two issues were related. It took some time to diagnose, and we have only recently concluded by our staff, external security consultants, and software vendors, that they were unrelated issues.
Do you know who accessed the information illegally?
No, the identity of the individual(s) responsible for this incident is still being investigated; however, they refer to themselves as "Scavenger" and the "whmcssec" team.
Is the stolen information being misused?
At this time, there is no evidence that your information has been misused.
SmartHost has not received any reports of misuse of specific individual’s personal information as a result of this incident.
We understand that this same individual(s) have conducted systematic similar breaches recently of hundreds of other web hosting providers in the industry.
It is our understanding that the system breach was done to prove a point, and force hosting providers to make security policy/procedure changes.
Does this mean I am a victim of identity theft or identity fraud?
No. This means that some personal information is in the hands of unauthorized individual(s), and they could use it to commit identity theft or identity fraud.
If you believe you are the victim of identity theft or fraud, you should immediately report it to local law enforcement.
What You Can Do
There is no reason to believe that you need to take necessary action at this time regarding the personal contact information.
We do recommend again changing your login passwords to the client/billing interface, and to any server/system provided with your SmartHost service, in case global resets did not complete such.
We also recommend implementing two-factor authentication (2FA) on your account, if not done so already, which can be done at: https://www.smarthost.net/index.php?rp=/user/security
As a best practice, we recommend you remain vigilant and promptly report any suspicious activity, or suspected identity theft, to the proper law enforcement authorities and financial and banking service providers.
On behalf of SmartHost, we apologize for this security breach and for any concern this may have caused.
We have subsequently taken, and continue to take, a number actions to ensure that this incident is thoroughly resolved, and to minimize the risk of a similar incident recurring
If you have any further questions, you are welcome to contact us by responding to this email notification.
SmartHost LLC
Henderson, NV USA http://smarthost.net [email protected]
@Brueggus said:
This just arrived. No message from LetBox so far.
Notice of Cybersecurity Incident
Attn: John Doe -
We are writing to notify you of a recent event that may have impacted your personal information.
At this time, we have no indication of fraudulent use of your personal information as a result of this incident.
Nevertheless, we are notifying you out of an abundance of caution to explain the circumstances as we understand them.
What Happened
SmartHost LLC recently became aware in late December 2023 of a cybersecurity incident impacting its client/billing platform.
An individual(s) accessed SmartHost's client/billing system administrative areas without authorization, including gaining access via a 3rd party vendor module.
(...snip...)
should've done this from the start. no need to do mental gymnastic until getting called out by treesmokah lol.
@Brueggus said:
This just arrived. No message from LetBox so far.
Notice of Cybersecurity Incident
Attn: John Doe -
We are writing to notify you of a recent event that may have impacted your personal information.
At this time, we have no indication of fraudulent use of your personal information as a result of this incident.
Nevertheless, we are notifying you out of an abundance of caution to explain the circumstances as we understand them.
What Happened
SmartHost LLC recently became aware in late December 2023 of a cybersecurity incident impacting its client/billing platform.
An individual(s) accessed SmartHost's client/billing system administrative areas without authorization, including gaining access via a 3rd party vendor module.
The individual(s) claimed to have downloaded customer data from SmartHost's computer systems, then threatened to post and disclose the data on an Internet forum.
Upon being made initially aware of a potential breach, SmartHost immediately began an investigation into the incident.
Although no data has been released that we have seen by this individual(s) as of this time, SmartHost has determined the client/billing system was indeed breached.
What information was potentially accessed?
The compromised data would include client names, address information, phone numbers, email addresses, user names, and account/service passwords
SmartHost does not store financial information on this platform, such as credit/debit card information, which would be stored directly with our 3rd party credit card processor.
SmartHost does not have any more sensitive information about our client base such as financial information, social security numbers, ID numbers, drivers license information, etc...
What We Are Doing
We take the security of our customers’ data seriously, and after SmartHost became aware of the event, we took immediate measures to investigate and remediate the incident.
We have implemented additional safeguards to improve security related to 3rd party software/modules, and the client/billing platform as a whole.
When SmartHost was made aware of the potential breach, we immediately performed global password resets for all client accounts and the server/service passwords that we could.
We also updated all internal system access methods/connectivity.
We have also hired external security consultants to review the matter and assist as well.
Please be assured that we take data security and confidentiality very seriously.
Steps SmartHost has taken to implement additional layers of security (not necessarily in this order):
Identified/removed the primary vulnerability associated with this incident
Global password resets for all users/systems
Update platform security settings and access credentials
Collaborated with cybersecurity specialists to review the situation
Reinstall clean system platform
Notified client base about the incident
Strengthen login credentials/methods and continue to enhance login protocols/procedures and other security measures
Continuing to monitor the situation and investigate this incident
Why did it take SmartHost so long to notify me about this?
SmartHost’s investigation is ongoing. As soon as SmartHost learned that its environment had been accessed by an unauthorized party, SmartHost immediately commenced the investigation, including working with third-party security consultants. System lockdowns were immediately implemented even before we could completely verify the breach. Simultaneously, SmartHost was dealing with another security issue at the same time, including DDOS/hack attempts against our VPS service platform, and we were unsure how/if the two issues were related. It took some time to diagnose, and we have only recently concluded by our staff, external security consultants, and software vendors, that they were unrelated issues.
Do you know who accessed the information illegally?
No, the identity of the individual(s) responsible for this incident is still being investigated; however, they refer to themselves as "Scavenger" and the "whmcssec" team.
Is the stolen information being misused?
At this time, there is no evidence that your information has been misused.
SmartHost has not received any reports of misuse of specific individual’s personal information as a result of this incident.
We understand that this same individual(s) have conducted systematic similar breaches recently of hundreds of other web hosting providers in the industry.
It is our understanding that the system breach was done to prove a point, and force hosting providers to make security policy/procedure changes.
Does this mean I am a victim of identity theft or identity fraud?
No. This means that some personal information is in the hands of unauthorized individual(s), and they could use it to commit identity theft or identity fraud.
If you believe you are the victim of identity theft or fraud, you should immediately report it to local law enforcement.
What You Can Do
There is no reason to believe that you need to take necessary action at this time regarding the personal contact information.
We do recommend again changing your login passwords to the client/billing interface, and to any server/system provided with your SmartHost service, in case global resets did not complete such.
We also recommend implementing two-factor authentication (2FA) on your account, if not done so already, which can be done at: https://www.smarthost.net/index.php?rp=/user/security
As a best practice, we recommend you remain vigilant and promptly report any suspicious activity, or suspected identity theft, to the proper law enforcement authorities and financial and banking service providers.
On behalf of SmartHost, we apologize for this security breach and for any concern this may have caused.
We have subsequently taken, and continue to take, a number actions to ensure that this incident is thoroughly resolved, and to minimize the risk of a similar incident recurring
If you have any further questions, you are welcome to contact us by responding to this email notification.
SmartHost LLC
Henderson, NV USA http://smarthost.net [email protected]
I've also received a message concerning the hack from letbox.
I didn't intend to renew my services because of the lack of communication,now I'm hesitating.
@remy said: I didn't intend to renew my services because of the lack of communication,now I'm hesitating.
If you are thinking about it, I'm sorry, but there is no hope for you.
I don't want to be mean, but after all of this shitshow, buying anything from them is the last thing I would be thinking of.
Do whatever you like, stay safe. There is no shortage of good providers for similar money.
@Brueggus said:
This just arrived. No message from LetBox so far.
Notice of Cybersecurity Incident
Attn: John Doe -
We are writing to notify you of a recent event that may have impacted your personal information.
At this time, we have no indication of fraudulent use of your personal information as a result of this incident.
Nevertheless, we are notifying you out of an abundance of caution to explain the circumstances as we understand them.
What Happened
SmartHost LLC recently became aware in late December 2023 of a cybersecurity incident impacting its client/billing platform.
An individual(s) accessed SmartHost's client/billing system administrative areas without authorization, including gaining access via a 3rd party vendor module.
The individual(s) claimed to have downloaded customer data from SmartHost's computer systems, then threatened to post and disclose the data on an Internet forum.
Upon being made initially aware of a potential breach, SmartHost immediately began an investigation into the incident.
Although no data has been released that we have seen by this individual(s) as of this time, SmartHost has determined the client/billing system was indeed breached.
What information was potentially accessed?
The compromised data would include client names, address information, phone numbers, email addresses, user names, and account/service passwords
SmartHost does not store financial information on this platform, such as credit/debit card information, which would be stored directly with our 3rd party credit card processor.
SmartHost does not have any more sensitive information about our client base such as financial information, social security numbers, ID numbers, drivers license information, etc...
What We Are Doing
We take the security of our customers’ data seriously, and after SmartHost became aware of the event, we took immediate measures to investigate and remediate the incident.
We have implemented additional safeguards to improve security related to 3rd party software/modules, and the client/billing platform as a whole.
When SmartHost was made aware of the potential breach, we immediately performed global password resets for all client accounts and the server/service passwords that we could.
We also updated all internal system access methods/connectivity.
We have also hired external security consultants to review the matter and assist as well.
Please be assured that we take data security and confidentiality very seriously.
Steps SmartHost has taken to implement additional layers of security (not necessarily in this order):
Identified/removed the primary vulnerability associated with this incident
Global password resets for all users/systems
Update platform security settings and access credentials
Collaborated with cybersecurity specialists to review the situation
Reinstall clean system platform
Notified client base about the incident
Strengthen login credentials/methods and continue to enhance login protocols/procedures and other security measures
Continuing to monitor the situation and investigate this incident
Why did it take SmartHost so long to notify me about this?
SmartHost’s investigation is ongoing. As soon as SmartHost learned that its environment had been accessed by an unauthorized party, SmartHost immediately commenced the investigation, including working with third-party security consultants. System lockdowns were immediately implemented even before we could completely verify the breach. Simultaneously, SmartHost was dealing with another security issue at the same time, including DDOS/hack attempts against our VPS service platform, and we were unsure how/if the two issues were related. It took some time to diagnose, and we have only recently concluded by our staff, external security consultants, and software vendors, that they were unrelated issues.
Do you know who accessed the information illegally?
No, the identity of the individual(s) responsible for this incident is still being investigated; however, they refer to themselves as "Scavenger" and the "whmcssec" team.
Is the stolen information being misused?
At this time, there is no evidence that your information has been misused.
SmartHost has not received any reports of misuse of specific individual’s personal information as a result of this incident.
We understand that this same individual(s) have conducted systematic similar breaches recently of hundreds of other web hosting providers in the industry.
It is our understanding that the system breach was done to prove a point, and force hosting providers to make security policy/procedure changes.
Does this mean I am a victim of identity theft or identity fraud?
No. This means that some personal information is in the hands of unauthorized individual(s), and they could use it to commit identity theft or identity fraud.
If you believe you are the victim of identity theft or fraud, you should immediately report it to local law enforcement.
What You Can Do
There is no reason to believe that you need to take necessary action at this time regarding the personal contact information.
We do recommend again changing your login passwords to the client/billing interface, and to any server/system provided with your SmartHost service, in case global resets did not complete such.
We also recommend implementing two-factor authentication (2FA) on your account, if not done so already, which can be done at: https://www.smarthost.net/index.php?rp=/user/security
As a best practice, we recommend you remain vigilant and promptly report any suspicious activity, or suspected identity theft, to the proper law enforcement authorities and financial and banking service providers.
On behalf of SmartHost, we apologize for this security breach and for any concern this may have caused.
We have subsequently taken, and continue to take, a number actions to ensure that this incident is thoroughly resolved, and to minimize the risk of a similar incident recurring
If you have any further questions, you are welcome to contact us by responding to this email notification.
SmartHost LLC
Henderson, NV USA http://smarthost.net [email protected]
@remy said: I didn't intend to renew my services because of the lack of communication,now I'm hesitating.
If you are thinking about it, I'm sorry, but there is no hope for you.
I don't want to be mean, but after all of this shitshow, buying anything from them is the last thing I would be thinking of.
Do whatever you like, stay safe. There is no shortage of good providers for similar money.
Any other provider could have been affected.
I seriously doubt that all low-cost providers have the resources to audit all the plugins they use.
On the other hand, what I would have appreciated was a brief communication to report the incident very quickly and to say that a more complete investigation was underway.
Rather than not communicating anything.
@remy said: Any other provider could have been affected.
They got breached by 2 different actors, in the same month. It requires some "skill".
@remy said: I seriously doubt that all low-cost providers have the resources to audit all the plugins they use.
Define low-cost, there are many great providers with custom non-WHMCS panels, actual security teams and competent developers, and its possible to get them for decent money.
When I see WHMCS my first thought is laziness, I value providers doing stuff on their own and not recycling shit everyone else uses that enables such "supply chain attacks".
Relying on proprietary panel, billing, provisioning systems, and so on with your entire business is the last thing I would do. Especially when WHMCS is known to not be very secure, and its always been like that.
As a host the least you could do is offer unique experience by providing custom software, especially as a VPS provider.
All of this is my personal opinion and you are of course free to think otherwise. There are providers who took steps to assure their WHMCS is secure and even if anything was breached, there is basically nothing in the database besides random emails.
@remy said: On the other hand, what I would have appreciated was a brief communication to report the incident very quickly and to say that a more complete investigation was underway.
Rather than not communicating anything.
This is the most "proper" way to handle it, and its been like that in "corporate" world for a long time.
Its the best you can do really, as soon as you spot a leakage, immediately let your customers know so they can act accordingly.
I'm not gonna pretend I'm a lawyer, but there are certain regulations in most States and Countries which specify time until which you have to let your customers know. The most time that was given in US, from what I remember, was 2 weeks, and SmartHost/Letbox took a month.
And its not like they spotted it themselves, the attacker did his best to reach them, despite being ignored at first. If not that, I bet they wouldn't know it happened to this day.
Just going to say I think the notification arriving so late is disappointing. Grateful that something finally has gone out, but once the issue was identified and initial remediations in place, customers should have been notified. You don’t need all information at hand and I believe it’s better to notify there appears to be an incident but you don’t yet understand the extent, than say nothing. Perhaps the status page was being used as a communication tool, but I had no reason to be accessing that without prior notice directing my attention there for updates.
@Richard said: Perhaps the status page was being used as a communication tool, but I had no reason to be accessing that without prior notice directing my attention there for updates.
Just to clarify, information on status page was related to the first hack, there was no information anywhere about WHMCS breach. This email is the first official mention of it.
@treesmokah said:
Define low-cost, there are many great providers with custom non-WHMCS panels, actual security teams and competent developers, and its possible to get them for decent money.
When I see WHMCS my first thought is laziness, I value providers doing stuff on their own and not recycling shit everyone else uses that enables such "supply chain attacks".
Maybe you can name a few?
I can think of a few, but not that many.
In fact it doesn't necessarily bother me that a provider uses proprietary software that is fairly common in the industry.
Let's just say that their core business isn't necessarily developing software. It's necessarily better if they control the whole chain, if it's done well.
You need skills to do that properly. You're less of a vector for attacks because you're the only one using your software, but on the other hand your software is much less audited and so errors can just as easily creep in.
There is one thing that bothers me though. It's that the delay in notifying gives the impression that they wanted to sweep it under the carpet.
And that's unacceptable. That's why I have mixed feelings about it.
@Calypso said:
Yes, I can imagine that you have a priority to get the hacker out, and repair stuff, but on the other side of things: communicate with your users. I haven't seen anything. If a hacker has gained access to your systems, you should always keep your customers informed - that's even mandatory in a lot of countries.
So...I suppose the network status incident that we kept updated non-stop, and quoted by the OP even in this thread, didn't exist?
What is with people these days...making assumptions without any knowledge, and not even capable of reading.
Let me help you out:
The OP posted info from our network status information that was consistently updated with what status and steps were being taken regarding a ddos/hack attack our VPS platform was having. We literally posted tons of updates there as it was underway. At this point most of it consolidated and the update by update listing consolidated and/or removed. Clients were fully and non-stop informed here, and pointed to such with any support tickets as well.
Let me help you out:
My VPS was down for quite some time earlier this month: over 6 hours. I tried to reach your site: also unreachable. When finally I was able to reach your portal, the first thing I checked was network status. Nothing. Absolutely nothing. Cause for that? I don't know: could be that it wasn't updated (yet), could also be that website was restored from an old backup. But I know what I've seen: no network downtime reported in the network status.
Basically what you are trying to say is "you are wrong customer". No, I am not, I'm not stupid. OP can have that information from the website, yes. But my ticket was from before that time, and not a few hours, no a couple of days. A few days later (after this topic was opened) the ticket wat "answered" with a simple "Services restored" and some ping data. Yeah, can see that myself. Not a single word about what happened. The main reason I made the ticket was that it was not the first downtime: 28th of December over 7 hours, and during the days before average packet loss was over 30%. Not a word about those has come back in the ticket.
Also sending out a mail today to all(?) customers is a bit late don't you think when the incident was "late December". A bit late I think personally when personal information is involved in combination with a (what you say unrelated) quite large amount of unreachability of VPS. Especially when you have that many tickets, I'd say: first send a mail out to all your customers with what's going on, and mention the big pile of tickets so people can understand response times...
But no, you come here and changing words of a customer and saying that he's wrong. Way to go. I've never suggested that the downtime or hack didn't happen. I've just said that the communication about everything was lacking. And by only sending out a mail today to customers you're, in my opinion, comfirming that statement of me. What is it with hosting providers these days, they make assumptions and appear unable to read. O wait, that's what you accused me of... strange world...
@Brueggus said:
This just arrived. No message from LetBox so far.
I received this email from LetBox. Hum.
Notice of Cybersecurity Incident
Attn: O Great One -
We are writing to notify you of a recent event that may have impacted your personal information.
At this time, we have no indication of fraudulent use of your personal information as a result of this incident.
Nevertheless, we are notifying you out of an abundance of caution to explain the circumstances as we understand them.
What Happened
LetBox recently became aware in late December 2023 of a cybersecurity incident impacting its client/billing platform.
An individual(s) accessed LetBox LLC's client/billing system administrative areas without authorization, including gaining access via a 3rd party vendor module.
The individual(s) claimed to have downloaded customer data from LetBox's computer systems, then threatend to post and disclose the data on an Internet forum.
Upon being made initially aware of a potential breach, LetBox immediately began an investigation into the incident.
Although no data has been released that we have seen by this individual(s) as of this time, LetBox has determined the client/billing system was indeed breached.
What information was potentially accessed?
The compromised data would include client names, address information, phone numbers, email addresses, user names, and account/service passwords
LetBox does not store financial information on this platform, such as credit/debit card information, which would be stored directly with our 3rd party credit card processor.
LetBox does not have any more sensitive information about our client base such as financial information, social security numbers, ID numbers, drivers license information, etc...
What We Are Doing
We take the security of our customers’ data seriously, and after LetBox became aware of the event, we took immediate measures to investigate and remediate the incident.
We have implemented additional safeguards to improve security related to 3rd party software/modules, and the client/billing platform as a whole.
When LetBox was made aware of the potential breach, we immediately performed global password resets for all client accounts and the server/service passwords that we could.
We also updated all internal system access methods/connectivity.
We have also hired external security consultants to review the matter and assist as well.
Please be assured that we take data security and confidentiality very seriously.
Steps LetBox has taken to implement additional layers of security (not necessarily in this order):
Identified/removed the primary vulnerability associated with this incident
Global password resets for all users/systems
Update platform security settings and access credentials
Collaborated with cybersecurity specialists to review the situation
Reinstall clean system platform
Notified client base about the incident
Strengthen login credentials/methods and continue to enhance login protocols/procedures and other security measures
Continuing to monitor the situation and investigate this incident
Why did it take LetBox so long to notify me about this?
LetBox’s investigation is ongoing. As soon as LetBox learned that its environment had been accessed by an unauthorized party, LetBox immediately commenced the investigation, including working with third-party security consultants. System lockdowns were immediately implemented even before we could completely verify the breach. Simultaneously, LetBox was dealing with another security issue at the same time, including DDOS/hack attempts against our VPS service platform, and we were unsure how/if the two issues were related. It took some time to diagnose, and we have only recently concluded by our staff, external security consultants, and software vendors, that they were unrelated issues.
Do you know who accessed the information illegally?
No, the identity of the individual(s) responsible for this incident is still being investigated; however, they refer to themselves as "Scavenger" and the "whmcssec" team.
Is the stolen information being misused?
At this time, there is no evidence that your information has been misused.
LetBox has not received any reports of misuse of specific individual’s personal information as a result of this incident.
We understand that this same individual(s) have conducted systematic similar breaches recently of hundreds of other web hosting providers in the industry.
It is our understanding that the system breach was done to prove a point, and force hosting providers to make security policy/procedure changes.
Does this mean I am a victim of identity theft or identity fraud?
No. This means that some personal information is in the hands of unauthorized individual(s), and they could use it to commit identity theft or identity fraud.
If you believe you are the victim of identity theft or fraud, you should immediately report it to local law enforcement.
What You Can Do
There is no reason to believe that you need to take necessary action at this time regarding the personal contact information.
We do recommend again changing your login passwords to the client/billing interface, and to any server/system provided with your LetBox service, in case global resets did not complete such.
We also recommend implementing two-factor authentication (2FA) on your account, if not done so alrewady, which can be done at:
[redacted]
As a best practice, we recommend you remain vigilant and promptly report any suspicious activity, or suspected identity theft, to the proper law enforcement authorities and financial and banking service providers.
On behalf of LetBox, we apologize for this security breach and for any concern this may have caused.
We have subsequently taken, and continue to take, a number actions to ensure that this incident is thoroughly resolved, and to minimize the risk of a similar incident recurring
If you have any further questions, you are welcome to contact us by responding to this email notification.
Just a few from my head. Most providers I use/d, use custom panels.
It's not the same price range.
I'm not saying that it's not worth investing a little more.
But most of the providers mentioned don't / rarely make offers on LES / LET.
Thanks for the list though.
@remy said: But most of the providers mentioned don't / rarely make offers on LES / LET.
They do not cater to LowEndAudience which usually creates problems over funny amounts of money, and I respect that, not everyone has time to deal with LowEndMinds.
Many of the providers I listed cater to audience that needs resilience, no matter who hates you, they will host you and tell attackers to fuck off. There are not many providers with balls left, and many of listed ones certainly got them.
Mevspace in particular not only is resilient but also offers extremely nice prices on dedicated servers.
The same goes for Terrahost and their "entry" series, unmetered(no FUP) 1Gbps dedi for $40? I would take it any day, especially when they ignore DMCA and other funny "legal" threats and offer high capacity in-house ddos protection(which is extremely rare nowadays).
ml.cloud aka Media Land LLC, just google them Its as close to North Korea location as you gonna get, less than 2h by car.
So... I have an account on SmartHost. Inactive, for years, but there is still my PI there [just tested it by reset password - email arrived, didn't reset, didn't login].
I did not get any e-mail until now (it's like 7+ hours, kinda enough for mailing to go thru millions of e-mails) - did they send it only to active users?
@FrankZ do you have a service active (or recently?) on LETBOX? @Brueggus - same, what are you active (recent) service status for LB/SH?
Comments
Brother, they literally admitted to getting breached a few posts above it. Its also been confirmed in "providers forum" on OGF, they are in the spreadsheet with other compromised providers.
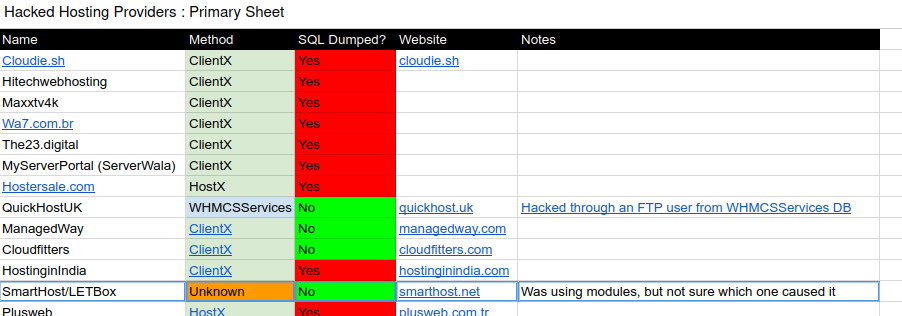
"SQL Dumped" stands for "leaked", their database is in possession of attackers.
So lets assume "ddos/hack" issue was separate from WHMCS breach "issue".
Its even more embarrassing this way, you got pwned 2 times in the same month. Presumably by 2 different attackers, both getting access to personal information and data of your customers.
First by someone who got access to VM's and client data on it, and then by someone who got access to people personal info from WHMCS.
Absolute fucking shitshow. Worst part is you didn't notify your clients about WHMCS breach, which was at this point close to a month ago. You could've send a notification, you could've submitted the data to HIBP, but you did none of that.
My recommendation from the other thread stays the same, stay away from this provider, they do not take personal information and security seriously. I have no idea what legal regulations are in the State you are located in, but some require to disclose a breach up to 2 weeks.
In EU you would've gotten sued to shit for all of that.
I guess I missed that. Tough to keep up. But I still don’t see it in that telegram channel, looking at files going back to Dec 26.
Do everything as though everyone you’ll ever know is watching.
All that was done so far was their WHMCS config and license getting leaked.
Attacker said he wont leak the entire database because "SmartHost notified the customers", I don't think he will be pleased to hear they didn't.
How did you get access to the spreadsheet?
FYI ANYONE.
That spreadsheet is just gathering and findings. We dont know if the attacker gained full access to db/configuration file.
EDIT: Attacker dumped configuration files of Letbox and Smarthost on TG.
So Biloh didn't tell anyone about the breach?
/s
It was circulating in certain communities for quite some time now, this screenshot is all I have. I had details on exploits used and how to deploy them a long time ago as well
Information should be free. Its on providers for not taking security seriously and not patching in time.
You shouldn't think "providers section" is private in any shape or form, given enough resources anyone can get access to whatever they want. Getting "Host Rep" on non-existent hosting provider isn't hard either.
Its safe to assume all passwords and keys are changed already, so I'm posting this screenshot.
censor parts of credentials, else you're going against rules of LES. Stay safe lol
is this proof that letbox got hacked?
I bench YABS 24/7/365 unless it's a leap year.
There is no way they are this dumb and didn't change it. If they didn't, oh well.
All I'm posting is a wall of meaningless text. Everything is public.
edit, censored.
Probably. But if you wanted to play devil's advocate, faking a configuration.php file would be like no effort. So, to be fair, probably based on what we've seen thus far but it's not impossible that they didn't.
Do everything as though everyone you’ll ever know is watching.
This just arrived. No message from LetBox so far.
dnscry.pt - Public DNSCrypt resolvers hosted by LowEnd providers • Need a free NAT LXC? -> https://microlxc.net/
should've done this from the start. no need to do mental gymnastic until getting called out by treesmokah lol.
LowEndDisclosure
Fuck this 24/7 internet spew of trivia and celebrity bullshit.
Well written Email, all I can say.
I've also received a message concerning the hack from letbox.
I didn't intend to renew my services because of the lack of communication,now I'm hesitating.
If you are thinking about it, I'm sorry, but there is no hope for you.
I don't want to be mean, but after all of this shitshow, buying anything from them is the last thing I would be thinking of.
Do whatever you like, stay safe. There is no shortage of good providers for similar money.
@SMARTHOST care to clarify
I bench YABS 24/7/365 unless it's a leap year.
Any other provider could have been affected.
I seriously doubt that all low-cost providers have the resources to audit all the plugins they use.
On the other hand, what I would have appreciated was a brief communication to report the incident very quickly and to say that a more complete investigation was underway.
Rather than not communicating anything.
They got breached by 2 different actors, in the same month. It requires some "skill".
Define low-cost, there are many great providers with custom non-WHMCS panels, actual security teams and competent developers, and its possible to get them for decent money.
When I see WHMCS my first thought is laziness, I value providers doing stuff on their own and not recycling shit everyone else uses that enables such "supply chain attacks".
Relying on proprietary panel, billing, provisioning systems, and so on with your entire business is the last thing I would do. Especially when WHMCS is known to not be very secure, and its always been like that.
As a host the least you could do is offer unique experience by providing custom software, especially as a VPS provider.
All of this is my personal opinion and you are of course free to think otherwise. There are providers who took steps to assure their WHMCS is secure and even if anything was breached, there is basically nothing in the database besides random emails.
This is the most "proper" way to handle it, and its been like that in "corporate" world for a long time.
Its the best you can do really, as soon as you spot a leakage, immediately let your customers know so they can act accordingly.
I'm not gonna pretend I'm a lawyer, but there are certain regulations in most States and Countries which specify time until which you have to let your customers know. The most time that was given in US, from what I remember, was 2 weeks, and SmartHost/Letbox took a month.
And its not like they spotted it themselves, the attacker did his best to reach them, despite being ignored at first. If not that, I bet they wouldn't know it happened to this day.
Just going to say I think the notification arriving so late is disappointing. Grateful that something finally has gone out, but once the issue was identified and initial remediations in place, customers should have been notified. You don’t need all information at hand and I believe it’s better to notify there appears to be an incident but you don’t yet understand the extent, than say nothing. Perhaps the status page was being used as a communication tool, but I had no reason to be accessing that without prior notice directing my attention there for updates.
Just to clarify, information on status page was related to the first hack, there was no information anywhere about WHMCS breach. This email is the first official mention of it.
So the hack was unrelated huh
Maybe you can name a few?
I can think of a few, but not that many.
In fact it doesn't necessarily bother me that a provider uses proprietary software that is fairly common in the industry.
Let's just say that their core business isn't necessarily developing software. It's necessarily better if they control the whole chain, if it's done well.
You need skills to do that properly. You're less of a vector for attacks because you're the only one using your software, but on the other hand your software is much less audited and so errors can just as easily creep in.
There is one thing that bothers me though. It's that the delay in notifying gives the impression that they wanted to sweep it under the carpet.
And that's unacceptable. That's why I have mixed feelings about it.
Let me help you out:
My VPS was down for quite some time earlier this month: over 6 hours. I tried to reach your site: also unreachable. When finally I was able to reach your portal, the first thing I checked was network status. Nothing. Absolutely nothing. Cause for that? I don't know: could be that it wasn't updated (yet), could also be that website was restored from an old backup. But I know what I've seen: no network downtime reported in the network status.
Basically what you are trying to say is "you are wrong customer". No, I am not, I'm not stupid. OP can have that information from the website, yes. But my ticket was from before that time, and not a few hours, no a couple of days. A few days later (after this topic was opened) the ticket wat "answered" with a simple "Services restored" and some ping data. Yeah, can see that myself. Not a single word about what happened. The main reason I made the ticket was that it was not the first downtime: 28th of December over 7 hours, and during the days before average packet loss was over 30%. Not a word about those has come back in the ticket.
Also sending out a mail today to all(?) customers is a bit late don't you think when the incident was "late December". A bit late I think personally when personal information is involved in combination with a (what you say unrelated) quite large amount of unreachability of VPS. Especially when you have that many tickets, I'd say: first send a mail out to all your customers with what's going on, and mention the big pile of tickets so people can understand response times...
But no, you come here and changing words of a customer and saying that he's wrong. Way to go. I've never suggested that the downtime or hack didn't happen. I've just said that the communication about everything was lacking. And by only sending out a mail today to customers you're, in my opinion, comfirming that statement of me. What is it with hosting providers these days, they make assumptions and appear unable to read. O wait, that's what you accused me of... strange world...
https://terrahost.com/
https://nicevps.net/
https://hosteam.pl/
https://4vps.su/
https://ml.cloud/
https://serveroffer.lt/
https://mevspace.com/
https://evoluso.com/
https://privatealps.net/
https://datawagon.com/ (never used, I do not endorse them)
Just a few from my head. Most providers I use/d, use custom panels.
v6node.com too. It's one of the best panels I've used. I really liked the UI.
The Ultimate Speedtest Script | Get Instant Alerts on new LES/LET deals | Cheap VPS Deals | VirMach Flash Sales Notifier
FREE KVM VPS - FreeVPS.org | FREE LXC VPS - MicroLXC
I received this email from LetBox. Hum.
Notice of Cybersecurity Incident
Attn: O Great One -
We are writing to notify you of a recent event that may have impacted your personal information.
At this time, we have no indication of fraudulent use of your personal information as a result of this incident.
Nevertheless, we are notifying you out of an abundance of caution to explain the circumstances as we understand them.
What Happened
LetBox recently became aware in late December 2023 of a cybersecurity incident impacting its client/billing platform.
An individual(s) accessed LetBox LLC's client/billing system administrative areas without authorization, including gaining access via a 3rd party vendor module.
The individual(s) claimed to have downloaded customer data from LetBox's computer systems, then threatend to post and disclose the data on an Internet forum.
Upon being made initially aware of a potential breach, LetBox immediately began an investigation into the incident.
Although no data has been released that we have seen by this individual(s) as of this time, LetBox has determined the client/billing system was indeed breached.
What information was potentially accessed?
The compromised data would include client names, address information, phone numbers, email addresses, user names, and account/service passwords
LetBox does not store financial information on this platform, such as credit/debit card information, which would be stored directly with our 3rd party credit card processor.
LetBox does not have any more sensitive information about our client base such as financial information, social security numbers, ID numbers, drivers license information, etc...
What We Are Doing
We take the security of our customers’ data seriously, and after LetBox became aware of the event, we took immediate measures to investigate and remediate the incident.
We have implemented additional safeguards to improve security related to 3rd party software/modules, and the client/billing platform as a whole.
When LetBox was made aware of the potential breach, we immediately performed global password resets for all client accounts and the server/service passwords that we could.
We also updated all internal system access methods/connectivity.
We have also hired external security consultants to review the matter and assist as well.
Please be assured that we take data security and confidentiality very seriously.
Steps LetBox has taken to implement additional layers of security (not necessarily in this order):
Identified/removed the primary vulnerability associated with this incident
Global password resets for all users/systems
Update platform security settings and access credentials
Collaborated with cybersecurity specialists to review the situation
Reinstall clean system platform
Notified client base about the incident
Strengthen login credentials/methods and continue to enhance login protocols/procedures and other security measures
Continuing to monitor the situation and investigate this incident
Why did it take LetBox so long to notify me about this?
LetBox’s investigation is ongoing. As soon as LetBox learned that its environment had been accessed by an unauthorized party, LetBox immediately commenced the investigation, including working with third-party security consultants. System lockdowns were immediately implemented even before we could completely verify the breach. Simultaneously, LetBox was dealing with another security issue at the same time, including DDOS/hack attempts against our VPS service platform, and we were unsure how/if the two issues were related. It took some time to diagnose, and we have only recently concluded by our staff, external security consultants, and software vendors, that they were unrelated issues.
Do you know who accessed the information illegally?
No, the identity of the individual(s) responsible for this incident is still being investigated; however, they refer to themselves as "Scavenger" and the "whmcssec" team.
Is the stolen information being misused?
At this time, there is no evidence that your information has been misused.
LetBox has not received any reports of misuse of specific individual’s personal information as a result of this incident.
We understand that this same individual(s) have conducted systematic similar breaches recently of hundreds of other web hosting providers in the industry.
It is our understanding that the system breach was done to prove a point, and force hosting providers to make security policy/procedure changes.
Does this mean I am a victim of identity theft or identity fraud?
No. This means that some personal information is in the hands of unauthorized individual(s), and they could use it to commit identity theft or identity fraud.
If you believe you are the victim of identity theft or fraud, you should immediately report it to local law enforcement.
What You Can Do
There is no reason to believe that you need to take necessary action at this time regarding the personal contact information.
We do recommend again changing your login passwords to the client/billing interface, and to any server/system provided with your LetBox service, in case global resets did not complete such.
We also recommend implementing two-factor authentication (2FA) on your account, if not done so alrewady, which can be done at:
[redacted]
As a best practice, we recommend you remain vigilant and promptly report any suspicious activity, or suspected identity theft, to the proper law enforcement authorities and financial and banking service providers.
On behalf of LetBox, we apologize for this security breach and for any concern this may have caused.
We have subsequently taken, and continue to take, a number actions to ensure that this incident is thoroughly resolved, and to minimize the risk of a similar incident recurring
If you have any further questions, you are welcome to contact us by responding to this email notification.
LetBox Limited
Henderson, NV USA
[redacted]
So now finally an email gets sent out. Slow as snails
It's not the same price range.
I'm not saying that it's not worth investing a little more.
But most of the providers mentioned don't / rarely make offers on LES / LET.
Thanks for the list though.
They do not cater to LowEndAudience which usually creates problems over funny amounts of money, and I respect that, not everyone has time to deal with LowEndMinds.
Many of the providers I listed cater to audience that needs resilience, no matter who hates you, they will host you and tell attackers to fuck off. There are not many providers with balls left, and many of listed ones certainly got them.
Mevspace in particular not only is resilient but also offers extremely nice prices on dedicated servers.
The same goes for Terrahost and their "entry" series, unmetered(no FUP) 1Gbps dedi for $40? I would take it any day, especially when they ignore DMCA and other funny "legal" threats and offer high capacity in-house ddos protection(which is extremely rare nowadays).
ml.cloud aka Media Land LLC, just google them Its as close to North Korea location as you gonna get, less than 2h by car.
Its as close to North Korea location as you gonna get, less than 2h by car.
So... I have an account on SmartHost. Inactive, for years, but there is still my PI there [just tested it by reset password - email arrived, didn't reset, didn't login].
I did not get any e-mail until now (it's like 7+ hours, kinda enough for mailing to go thru millions of e-mails) - did they send it only to active users?
@FrankZ do you have a service active (or recently?) on LETBOX?
@Brueggus - same, what are you active (recent) service status for LB/SH?
Haven't bought a single service in VirMach Great Ryzen 2022 - 2023 Flash Sale.
https://lowendspirit.com/uploads/editor/gi/ippw0lcmqowk.png